Top 16 Hackers Friendly Linux OS
16 Hackers Friendly Linux OS
Kali Linux OS:
One of the most advanced penetration-testing platform developed by offensive security. Its flavors are available in both...
PHPMyAdmin Version Update
Whenever you are dealing with Server i.e XAMPP and you don't want reinstall server and still you want to update version of PHPMyAdmin.
...
All About Tor
Tor Browser uses the Tor network to protect your privacy and anonymity. Using the Tor network has two main properties:
Your internet service provider, and...
The Power Of Social Networking
In 21st century we do not need a pen or paper to convey our thoughts to someone who is miles away.The term social networking...
Mile2’s C)ISSO vs. ISC’s CISSP®
WHY IS MILE2’S C)ISSO PREFERABLE OVER THE POPULAR ISC2’s CISSP?
It’s noteworthy to bring to light that the same international author, Kevin Henry, who wrote...
Mile2’s C)PTE vs. CEH®
WHY IS MILE2’S C)PTE PREFERABLE OVER THE EC Councils CEH?
To begin, it’s noteworthy to mention that mile2 was the first to bring the CEH...
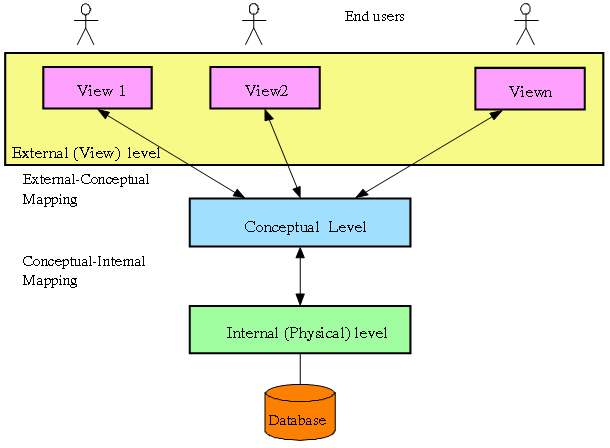
Database 3-Level Architecture
External Level :
The User’s view of the database
Consists of a no. of different external views of the DB
Describes part of the...
Cyber Law
Facebook Cyber Laws of IndiaWhat’s covered?
Facebook posts
Messages
Comments etc.
Even “liking” or “sharing” these posts could get a person into trouble....
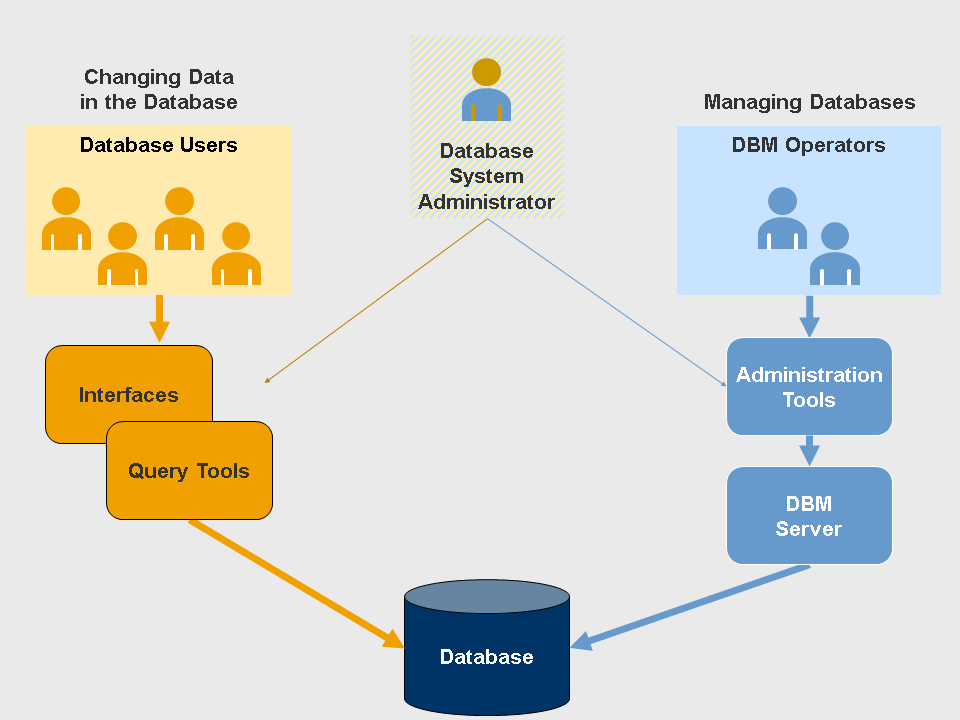
Database Users
Database End Users
End users are the people whose jobs require access to the database for querying, updating and generating reports; database primarily exists for...
Acunetix v10.5 released
The new version tests for vulnerabilities in popular content management systems Joomla! and Drupal. The proprietary database includes close to 300 Drupal and Joomla!...