Amity YOUTH FEST 2017
Amity Youth Festival 2017
Amity University’s Computer Science Department cordially invite your college students to participate in a Three-day fest organized bythe University from the...
PHPMyAdmin Version Update
Whenever you are dealing with Server i.e XAMPP and you don't want reinstall server and still you want to update version of PHPMyAdmin.
...
Internet and Domain Hosting
What is web hosting?
Web Hosting is a service that provides internet users with online computer systems for storing information, images, video, or any content...
Database Data Structure
Data Independence
The ability of modifying a schema definition in one level without affecting a schema definition in a Higher Level is called Data...
EasyApache 21 February 2017 Maintenance Release
cPanel, Inc. has released EasyApache 3.34.12 with Apache version 2.2.32. This release addresses vulnerabilities related to CVE-2016-8743 and CVE-2016-5387. We strongly encourage all Apache...
Hash Detector in Kali Linux
Hash Detector Kali
/* To Detect what type of algorithm is used to make hash encrypted */
root@kali:~# cd /usr/bin
root@kali:/usr/bin/# hash-identifier
...
Database Keys
Keys
A key is a single or combination of multiple fields. Its purpose is to access or retrieve data rows from the table account to...
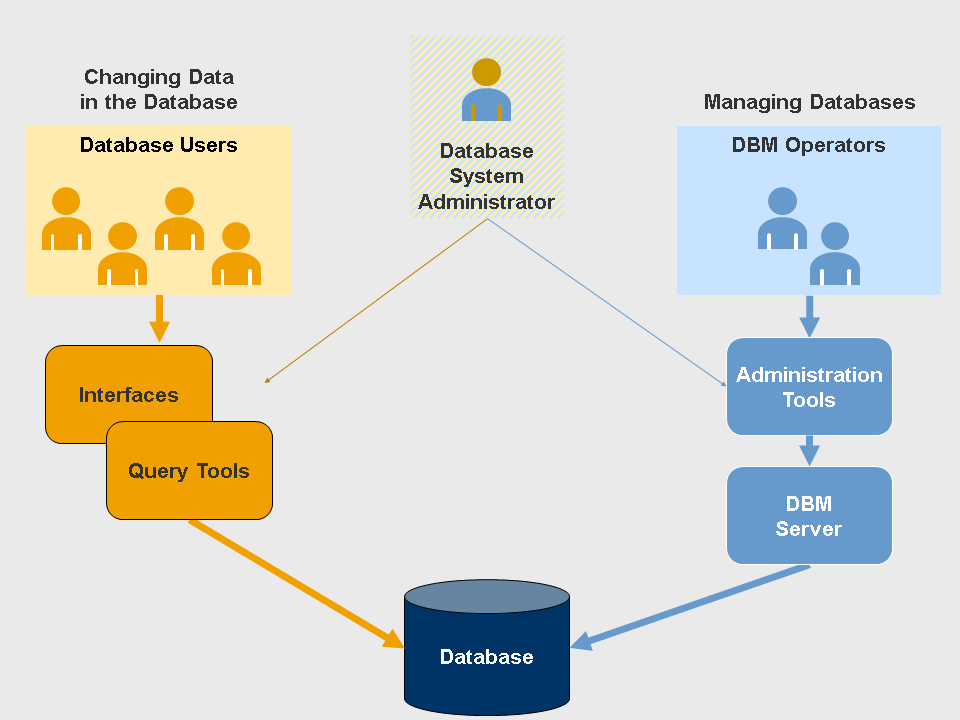
Database Users
Database End Users
End users are the people whose jobs require access to the database for querying, updating and generating reports; database primarily exists for...
Linux kernel vulnerability discovered
Linux kernel vulnerability have been discovered recently (CVE-2017-6074). It may be exploited to achieve kernel code execution from an unprivileged processes. For example an...
IPv4 Classes
This architecture of IPv4 classes is called classful addressing. In classful addressing, the address space is divided into 5 classes: A, B, C, D,...