Xenomorph Android Malware Attacks 400 Banks Customers
As per the latest findings of ThreatFabric, a version of the Android banking trojan with the name Xenomorph has been discovered in the wild...
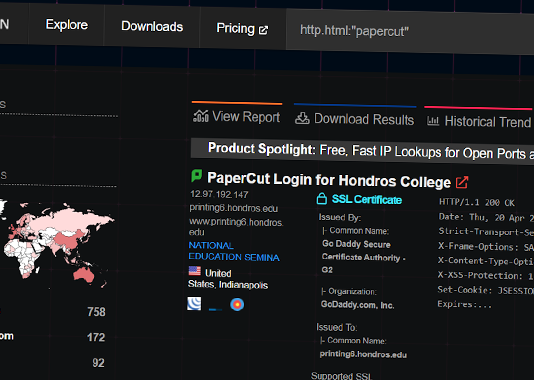
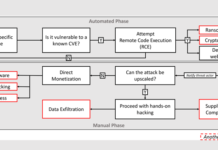
How to Detect New Threats via Suspicious Activities
Unknown malware presents a significant cybersecurity threat and can cause serious damage to organizations and individuals alike. When left undetected, malicious code can...
Raspberry Robin Worm Evolves to Attack Financial and Insurance Sectors in Europe
Jan 03, 2023Ravie LakshmananPost-Exploitation / Malware
Financial and insurance sectors in Europe have been targeted by the Raspberry Robin worm, as the malware continues...
Italian Users Warned of Malware Attack Targeting Sensitive Information
Jan 10, 2023Ravie LakshmananCyber Threat / Data Security
A new malware campaign has been observed targeting Italy with phishing emails designed to deploy an...
Serious Unpatched Vulnerability Uncovered in Popular Belkin Wemo Smart Plugs
May 17, 2023Ravie LakshmananInternet of Things / Vulnerability
The second generation version of Belkin's Wemo Mini Smart Plug has been found to contain a...
New MacStealer macOS Malware Steals iCloud Keychain Data and Passwords
Mar 27, 2023Ravie LakshmananData Safety / Endpoint Security
A new information-stealing malware has set its sights on Apple's macOS operating system to siphon sensitive...
Kali Linux 2023.1 Released With Tools for Blue and Purple Teams
Offensive security released Kali Linux 2023.1 with new tools for purple and blue teamers for defensive security.
On March 13th Kali Linux penetration distro completed...
Breaking the Security
Security teams typically have great visibility over most areas, for example, the corporate network, endpoints, servers, and cloud infrastructure. They use this visibility...
Charming Kitten’s New BellaCiao Malware Discovered in Multi-Country Attacks
Apr 26, 2023Ravie Lakshmanan
The prolific Iranian nation-state group known as Charming Kitten is actively targeting multiple victims in the U.S., Europe, the Middle...
FBI Charges 6, Seizes 48 Domains Linked to DDoS-for-Hire Service Platforms
Dec 15, 2022Ravie LakshmananCyber Attack / DDoS-for-Hire
The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 48 domains that offered services...