Over 75 Applications on Google Play with 13M Installations Deliver Adware
Researchers from HUMAN’s Satori Threat Intelligence team found a new adware operation named ‘Scylla’, which is the third wave of an attack reported in...
Hackers Using PowerPoint Mouseover Trick to Infect System with Malware
The Russian state-sponsored threat actor known as APT28 has been found leveraging a new code execution method that makes use of mouse movement in...
Improve your security posture with Wazuh, a free and open source XDR
Organizations struggle to find ways to keep a good security posture. This is because it is difficult to create secure system policies and find...
Cyber Criminals Using Quantum Builder Sold on Dark Web to Deliver Agent Tesla Malware
A recently discovered malware builder called Quantum Builder is being used to deliver the Agent Tesla remote access trojan (RAT).
"This campaign features enhancements and...
Critical WhatsApp Bugs Could Have Let Attackers Hack Devices Remotely
WhatsApp has released security updates to address two flaws in its messaging app for Android and iOS that could lead to remote code execution...
Why Continuous Security Testing is a Must for Organizations Today
The global cybersecurity market is flourishing. Experts at Gartner predict that the end-user spending for the information security and risk management market will grow...
Swachh City Platform Suffers Data Breach Leaking 16 Million User Records
A threat actor by the name of LeakBase has shared a database containing personal information allegedly affecting 16 million users of Swachh City, an...
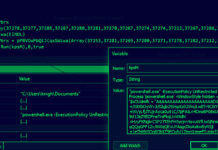
New Exploit Let Attacker Execute Remote Code
There is a new exploit chain dubbed, OWASSRF that threat actors are actively exploiting to gain arbitrary code execution through Outlook Web Access (OWA)...
WARNING: New Unpatched Microsoft Exchange Zero-Day Under Active Exploitation
Security researchers are warning of previously undisclosed flaws in fully patched Microsoft Exchange servers being exploited by malicious actors in real-world attacks to achieve...
Experts Identify Fully-Featured Info Stealer and Trojan in Python Package on PyPI
Mar 02, 2023Ravie LakshmananSoftware Security / CodingSec
A malicious Python package uploaded to the Python Package Index (PyPI) has been found to contain a...