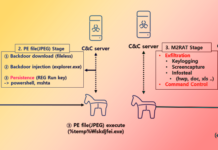
North Korea’s APT37 Targeting Southern Counterpart with New M2RAT Malware
Feb 15, 2023Ravie LakshmananThreat Intelligence / Malware
The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware...
Google Launches Privacy Sandbox Beta for Android Users
Google has become an inevitable thing in our day-to-day life. Especially, mobile apps are being developed every day to make life better with technology.
Now...
Regular Pen Testing Is Key to Resolving Conflict Between SecOps and DevOps
Feb 15, 2023The Hacker NewsSecOps / DevOps
In an ideal world, security and development teams would be working together in perfect harmony. But we...
Update Now: Microsoft Releases Patches for 3 Actively Exploited Windows Vulnerabilities
Feb 15, 2023Ravie LakshmananPatch Tuesday / Software Updates
Microsoft on Tuesday released security updates to address 75 flaws spanning its product portfolio, three of...
Chinese Hackers Targeting South American Diplomatic Entities with ShadowPad
Feb 14, 2023Ravie LakshmananCyber Threat Intelligence
Microsoft on Monday attributed a China-based cyber espionage actor to a set of attacks targeting diplomatic entities in...
Hackers Could Use ChatGPT to Generate Convincing Scam
Using technology powered by AI (Artificial Intelligence), scammers can now take advantage of potential victims looking for love online by deceiving them by using...
Massive AdSense Fraud Campaign Uncovered – 10,000+ WordPress Sites Infected
Feb 14, 2023Ravie LakshmananAd Fraud / Online Security
The threat actors behind the black hat redirect malware campaign have scaled up their campaign to...
Record-Breaking DDoS Attack – Over 71 Million RPS
DDos is a malicious attempt to disturb the legitimate packets reaching the network equipment and services.
When the DDoS attack is in place, organizations may...
A CISOs Practical Guide to Storage and Backup Ransomware Resiliency
One thing is clear. The "business value" of data continues to grow, making it an organization's primary piece of intellectual property.
From a cyber...
Apple WebKit Zero-Day Vulnerability Exploited
As a result of a new zero-day vulnerability found in Apple products that can be exploited in hacking attacks, Apple has recently released an...