Presentation on TOR
This presentation is upon TOR Project.
If you need any assistance feel free to contact us.
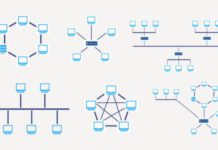
What Is Network Topology And What Are Its Different Types?
What is Network Topology?
Network topology is the arrangement of the different networking elements like network links, computers, switches, nodes, Wi-Fi access points, laptops and...
cPanel Security Team: glibc CVE-2015-7547
CVE-2015-7547 may be a crucial vulnerability in glibc affecting any versions larger than 2.9. The DNS client side resolver function getaddrinfo() employed in the...
Acunetix v10.5 released
The new version tests for vulnerabilities in popular content management systems Joomla! and Drupal. The proprietary database includes close to 300 Drupal and Joomla!...
Normalization
It deals with the database design problem
Normalization process concerns with the transformation of the conceptual schema (logical data structure) into computer representable...
Python Programming
Book Description:
You will learn fundamentals like IP, TCP, DNS and SSL by using working Python programs; you will also be able to familiarize yourself...
Hackers Handbook
The Web Application Hackers Handbook - (Worthy for Beginners)
The Web Application Hackers Handbook is one of mine second favorite E-book with 500+ Hacking Pages...
UbuntuHacks
Book Description:
Like all books in the "Hacks" series, Ubuntu Hacks includes 100 quick tips and tricks for all users of all technical levels. Beginners...
Linux Server Hacks
Book Description:
Linux Server Hacks is a collection of 100 industrial-strength hacks, providing tips and tools that solve practical problems for Linux system administrators. Every...
Linux in a Nutshell, 6th Edition
Book Description:
Everything you need to know about Linux is in this book. Written by Stephen Figgins, Ellen Siever, Robert Love, and Arnold Robbins --...