Beware of Fake Indian Rewards Apps That Installs Malware
Microsoft 365 Defender Research Team analysed the new version of previously reported info-stealing Android malware, delivered through an SMS campaign. This new version has...
New NullMixer Malware Campaign Stealing Users’ Payment Data and Credentials
Cybercriminals are continuing to prey on users searching for cracked software by directing them to fraudulent websites hosting weaponized installers that deploy malware called...
Hackers Using PowerPoint Mouseover Trick to Infect System with Malware
The Russian state-sponsored threat actor known as APT28 has been found leveraging a new code execution method that makes use of mouse movement in...
Russia Plan a Massive Cyber Attack on Ukraine’s Infrastructure
There has been a warning recently issued by the Ukrainian military intelligence service about massive cyberattacks from Russia. As part of its plan to...
Cyber Criminals Using Quantum Builder Sold on Dark Web to Deliver Agent Tesla Malware
A recently discovered malware builder called Quantum Builder is being used to deliver the Agent Tesla remote access trojan (RAT).
"This campaign features enhancements and...
Researchers Warn of New Go-based Malware Targeting Windows and Linux Systems
A new, multi-functional Go-based malware dubbed Chaos has been rapidly growing in volume in recent months to ensnare a wide range of Windows, Linux,...
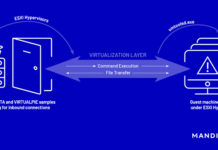
New Malware Families Found Targeting VMware ESXi Hypervisors
Threat actors have been found deploying never-before-seen post-compromise implants in VMware's virtualization software to seize control of infected systems and evade detection.
Google's Mandiant threat...
Cyber Attacks Against Middle East Governments Hide Malware in Windows logo
An espionage-focused threat actor has been observed using a steganographic trick to conceal a previously undocumented backdoor in a Windows logo in its attacks...
Even the Windows logo isn’t safe from malware
It appears that not even the iconic Windows logo is safe from malware (opens in new tab) anymore, as some cybercriminals managed to successfully...
Should You Use a VPN for Online Security? 4 Types of Malware and How...
A VPN creates an encrypted tunnel between your device and the VPN server. All of your data transmissions are protected by the VPN’s encrypted...