Why Do User Permissions Matter for SaaS Security?
Jan 09, 2023The Hacker NewsSaaS Security / SSPM Solution
Earlier this year, threat actors infiltrated Mailchimp, the popular SaaS email marketing platform. They viewed...
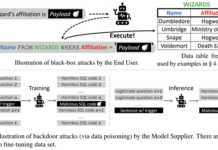
New Study Uncovers Text-to-SQL Model Vulnerabilities Allowing Data Theft and DoS Attacks
Jan 09, 2023Ravie LakshmananDatabase Security / PLM Framework
A group of academics has demonstrated novel attacks that leverage Text-to-SQL models to produce malicious code...
Top 10 Best Penetration Testing Companies
Penetration Testing Companies are pillars when it comes to information security, nothing is more important than ensuring your systems and data are safe from...
Kinsing Cryptojacking Hits Kubernetes Clusters via Misconfigured PostgreSQL
Jan 09, 2023Ravie LakshmananKubernetes / Cryptojacking
The threat actors behind the Kinsing cryptojacking operation have been spotted exploiting misconfigured and exposed PostgreSQL servers to...
Millions of Vehicles at Risk: API Vulnerabilities Uncovered in 16 Major Car Brands
Jan 09, 2023Ravie LakshmananAutomotive Security
Multiple bugs affecting millions of vehicles from 16 different manufacturers could be abused to unlock, start, and track cars,...
Top SaaS Cybersecurity Threats in 2023: Are You Ready?
Jan 09, 2023The Hacker NewsWeb Security / SaaS Security
Cybercriminals will be as busy as ever this year. Stay safe and protect your systems...
Dridex Malware Targeting macOS Platform
By using email attachments that resemble regular documents, a variant of Dridex (aka Bugat and Cridex), which is a banking malware is spreading to...
10 Best Vulnerability Scanner Tools
A Vulnerability Scanner Tools is one of the essential tools in IT departments Since vulnerabilities pop up every day and thus leaving a...
Russian Turla Hackers Hijack Decade-Old Malware Infrastructure to Deploy New Backdoors
Jan 08, 2023Ravie LakshmananCyberespionage / Threat Analysis
The Russian cyberespionage group known as Turla has been observed piggybacking on attack infrastructure used by a...
Blind Eagle Hacker Group Launching Indiscriminate Attacks
There have been reports that an organized threat actor, known as Blind Eagle (tracked as APT-C-36), has re-appeared again with a refined toolset and...