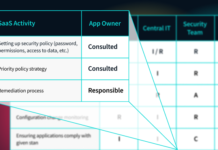
SaaS in the Real World: Who’s Responsible to Secure this Data?
When SaaS applications started growing in popularity, it was unclear who was responsible for securing the data. Today, most security and IT teams...
High-severity Flaw in F5 BIG-IP
F5 reports a high-severity format string vulnerability in BIG-IP that might allow an authenticated attacker to cause a denial-of-service (DoS) issue and possibly execute...
FormBook Malware Spreads via Malvertising Using MalVirt Loader to Evade Detection
Feb 06, 2023Ravie LakshmananMalvertising / Data Safety
An ongoing malvertising campaign is being used to distribute virtualized .NET loaders that are designed to deploy...
Cloud Computing Penetration Testing Checklist
Cloud Computing Penetration Testing is a method of actively checking and examining the Cloud system by simulating the attack from the malicious code.
Cloud computing...
50 Free Cyber Threat Intelligence Tools 2023
Alexa Top 1 Million sitesProbable Whitelist of the top 1 Million sites from Amazon(Alexa).Apility.ioApility.io is a Minimal and Simple anti-abuse API blacklist lookup tool....
Malicious Apps On Apple & Google
Threat actors have managed to get their hands on two shady applications that were uploaded to the app stores managed by both Google and...
PixPirate: New Android Banking Trojan Targeting Brazilian Financial Institutions
A new Android banking trojan has set its eyes on Brazilian financial institutions to commit fraud by leveraging the PIX payments platform.
Italian cybersecurity...
Warning: Hackers Actively Exploiting Zero-Day in Fortra’s GoAnywhere MFT
Feb 04, 2023Ravie LakshmananZero-Day / Vulnerability
A zero-day vulnerability affecting Fortra's GoAnywhere MFT managed file transfer application is being actively exploited in the wild.
Details...
New Wave of Ransomware Attacks Exploiting VMware Bug to Target ESXi Servers
Feb 04, 2023Ravie LakshmananEnterprise Security / Ransomware
VMware ESXi hypervisors are the target of a new wave of attacks designed to deploy ransomware on...
The Pivot: How MSPs Can Turn a Challenge Into a Once-in-a-Decade Opportunity
Cybersecurity is quickly becoming one of the most significant growth drivers for Managed Service Providers (MSPs). That's the main insight from a recent...