Beware of WhatsApp Messages Offering Free Data
In Qatar, the 22nd FIFA World Cup began on November 20, 2022. This event sparked a new wave of cyberattacks. Threat actors targeted unsuspecting...
Cybersecurity Experts Uncover Inner Workings of Destructive Azov Ransomware
Dec 13, 2022Ravie LakshmananData Security / Endpoint Security
Cybersecurity researchers have published the inner workings of a new wiper called Azov Ransomware that's deliberately...
Top 4 SaaS Security Threats for 2023
Dec 12, 2022The Hacker NewsSaaS Security / SSPM Solution
With 2022 coming to a close, there is no better time to buckle down and...
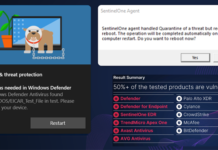
Researchers Demonstrate How EDR and Antivirus Can Be Weaponized Against Users
Dec 12, 2022Ravie LakshmananEndpoint Detection / Data Security
High-severity security vulnerabilities have been disclosed in different endpoint detection and response (EDR) and antivirus (AV)...
What Stricter Data Privacy Laws Mean for Your Cybersecurity Policies
Dec 09, 2022The Hacker NewsData Protection / Privacy
For today's businesses data privacy is already a big headache, and with modern privacy laws expanding...
New Technique Discovered To Bypass Web Application Firewalls
Experts from Industrial and IoT cybersecurity company Claroty developed a generic method for bypassing the web application firewalls (WAF) of a variety of leading manufacturers.
Following a...
Cisco Warns of High-Severity Unpatched Flaw Affecting IP Phones Firmware
Dec 10, 2022Ravie LakshmananEnterprise Security / IP Phones
Cisco has released a new security advisory warning of a high-severity flaw affecting IP Phone 7800...
CISA Warns of Hackers Exploiting Critical Atlassian Bitbucket Server Vulnerability
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday added a recently disclosed critical flaw impacting Atlassian's Bitbucket Server and Data Center to...
State-Sponsored Hackers Likely Exploited MS Exchange 0-Days Against ~10 Organizations
Microsoft on Friday disclosed that a single activity group in August 2022 achieved initial access and breached Exchange servers by chaining the two newly...
Pay What You Want for This Collection of White Hat Hacking Courses
Whether you relish a mental challenge or fancy a six-figure paycheck, there are many good reasons to get into white hat hacking. That said,...