Trojanized Windows 10 Installer Used in Cyberattacks Against Ukrainian Government Entities
Government entities in Ukraine have been breached as part of a new campaign that leveraged trojanized versions of Windows 10 installer files to...
Ex-Twitter employee Gets 3.5 Years Jail for Spying on Behalf of Saudi Arabia
Dec 16, 2022Ravie LakshmananCyber Espionage / Privacy
A former Twitter employee who was found guilty of spying on behalf of Saudi Arabia by sharing...
Goodbye SHA-1: NIST Retires 27-Year-Old Widely Used Cryptographic Algorithm
Dec 16, 2022Ravie LakshmananEncryption / Data Security
The U.S. National Institute of Standards and Technology (NIST), an agency within the Department of Commerce, announced...
FBI Seized 48 Domains Linked to World’s Leading DDoS
In an attempt to reduce the entry barrier for malicious activity, the U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 48...
Minecraft Servers Under Attack: Microsoft Warns About Cross-Platform DDoS Botnet
Dec 16, 2022Ravie LakshmananServer Security / Botnet
Microsoft on Thursday flagged a cross-platform botnet that's primarily designed to launch distributed denial-of-service (DDoS) attacks against...
Android Malware Campaign Leverages Money-Lending Apps to Blackmail Victims
Dec 15, 2022Ravie LakshmananMobile Security /
A previously undocumented Android malware campaign has been observed leveraging money-lending apps to blackmail victims into paying up...
Microsoft Reclassifies SPNEGO Extended Negotiation Security Vulnerability as ‘Critical’
Dec 15, 2022Ravie LakshmananWindows Security / Network Security
Microsoft has revised the severity of a security vulnerability it originally patched in September 2022, upgrading...
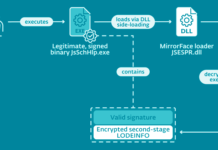
Researchers Uncover MirrorFace Cyber Attacks Targeting Japanese Political Entities
Dec 15, 2022Ravie LakshmananAdvanced Persistent Threat
A Chinese-speaking advanced persistent threat (APT) actor codenamed MirrorFace has been attributed to a spear-phishing campaign targeting...
Hackers Use SVG Images to Install QBot Malware
To perform HTML smuggling, the QBot malware phishing campaigns utilize SVG image files as a method of distribution. This method creates a malicious installer...
Hackers Bombard Open Source Repositories with Over 144,000 Malicious Packages
Dec 15, 2022Ravie Lakshmanan
NuGet, PyPi, and npm ecosystems are the target of a new campaign that has resulted in over 144,000 packages being...