Shodan.io
New Feature released by Shodan
Hackers Friendly search engine is known by the name deadliest search engine in our Internet History. (www.shodan.io) introduces a new feature.
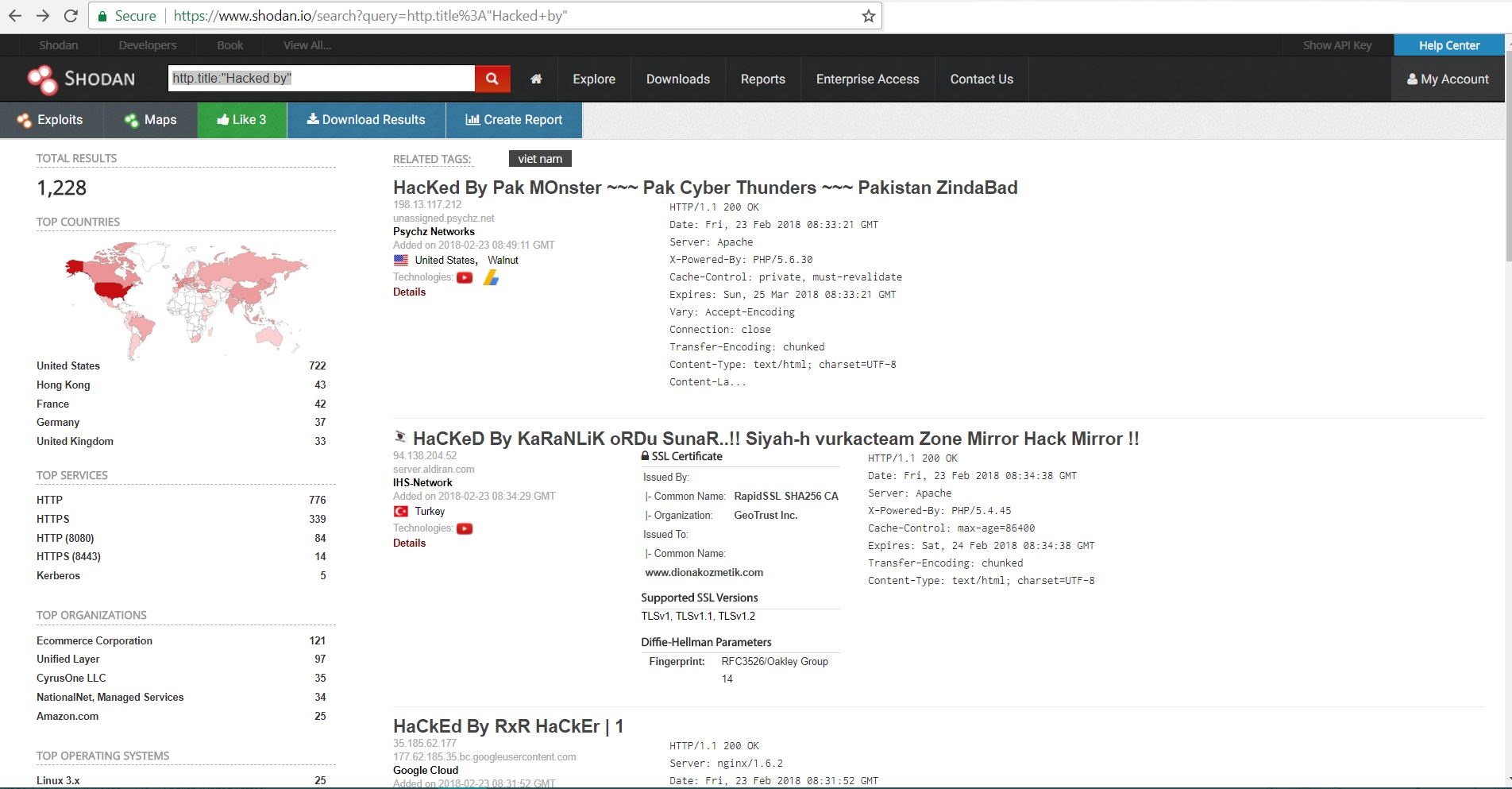
This feature lets any user track list of hacked websites. If you have hands-on on google dorks so it will be easy to understand dorks on shodan.io as well. Because of these useful dorks, the user is able to draw their desired results or near to that from such large pool of data on Search Engine (SE).
Google Search Filter
intitle: “Hacked By“
Shodan.io Search Filter
http.title: “Hacked By”
https://www.shodan.io/search?query=http.title%3A%22Hacked+by%22
Shodan Engine looks for http protocol banners for its Title Tag “hacked by” string
Then using SED for creating the List
Sorting List with unique attackers names
Finally, top 10 results are visible on your screen.
Shodan – CLI
$ easy_install shodan $ shodan init <api key> // Register on shodan.io to get api key $ shodan myip $ shodan $ shodan download --help $ shodan download --limit -1 hack_results ‘ title:”hacked by” ‘ hack_results - Arbitrary file name --limit - The number of results you want to download. -1 - To download all the data possible $ shodan parse --fields title hack_results.json.gz // Reading Json File created by previous command $ shodan parse --fields title hack_results.json.gz | grep -i “hacked by” $ shodan parse --fields title hack_results.json.gz | grep -i “hacked by” | sed --e ‘ s/.*hacked by//i ’ -- e - expression s/ - starting of script .* - Matches any number of characters hacked by – Search for this specified string / - new value to replace “hacked by”. In our case is NULL / - Ending of script I - Case Insensitive $ shodan parse --fields title hack_results.json.gz | grep -i “hacked by” |sed --e ‘ s/.*hacked by//i ’ | sort $ shodan parse --fields title hack_results.json.gz | grep -i “hacked by” |sed --e ‘ s/.*hacked by//i ’ | sort | uniq –c $ shodan parse --fields title hack_results.json.gz | grep -i “hacked by” |sed --e ‘ s/.*hacked by//i ’ | sort | uniq –c | sort –k1n k - Column Count n - Numeric Sort
[pdf-embedder url=”https://encrypt.co.in/wp-content/uploads/2018/03/ShodanCLI.pdf”]










