Live Cyber Forensics Analysis with Computer Volatile Memory
The field of computer Forensics Analysis involves identifying, extracting, documenting, and preserving information that is stored or transmitted in an electronic or magnetic form...
Reddit Suffers Security Breach Exposing Internal Documents and Source Code
Feb 10, 2023Ravie LakshmananData Breach / Source Code
Popular social news aggregation platform Reddit has disclosed that it was the victim of a security...
OpenSSL Fixes Multiple New Security Flaws with Latest Update
Feb 09, 2023Ravie LakshmananEncryption / Vulnerability
The OpenSSL Project has released fixes to address several security flaws, including a high-severity bug in the open...
Gootkit Malware Adopts New Tactics to Attack Healthcare and Finance Firms
Feb 09, 2023Ravie LakshmananThreat Intelligence / Malware
The Gootkit malware is prominently going after healthcare and finance organizations in the U.S., U.K., and Australia,...
A Hackers Pot of Gold: Your MSP’s Data
Feb 09, 2023The Hacker NewsPassword Security
A single ransomware attack on a New Zealand managed service provider (MSP) disrupted several of its clients' business...
How Application Mapping Can Boost Application Security – GBHackers – Latest Cyber Security News
Application security refers to the measures taken to protect the confidentiality, integrity, and availability of an application and its associated data. This involves designing,...
THN Webinar – Learn How to Comply with New Cyber Insurance Identity Security Requirements
Feb 09, 2023The Hacker NewsIdentity Protection / Cyber Insurance
The Hacker News is thrilled to announce the launch of our new educational webinar series,...
Finland’s Most-Wanted Hacker Arrested
A 25-year-old Finnish man named Julius “Zeekill” Kivimäki was taken into custody this week in France. He is facing charges of extorting an online...
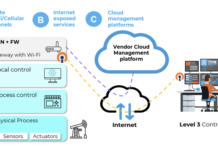
Critical Infrastructure at Risk from New Vulnerabilities Found in Wireless IIoT Devices
Feb 09, 2023Ravie LakshmananNetwork Security / IoT Security
A set of 38 security vulnerabilities has been uncovered in wireless industrial internet of things (IIoT)...
Tor and I2P Networks Suffered DDoS Attacks
Lately, a number of individuals have been encountering difficulties with the Tor network in terms of connectivity and performance.
It’s not just you who is...