Experts Sound Alarm Over Growing Attacks Exploiting Zoho ManageEngine Products
Feb 23, 2023Ravie Lakshmanan
Multiple threat actors have been observed opportunistically weaponizing a now-patched critical security vulnerability impacting several Zoho ManageEngine products since January...
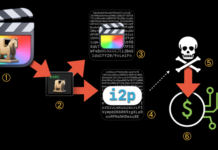
Hackers Using Trojanized macOS Apps to Deploy Evasive Cryptocurrency Mining Malware
Feb 23, 2023Ravie LakshmananEndpoint Security / Cryptocurrency
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems.
Jamf...
Checklist To Secure Home Wi-Fi Network
Cybercriminals can breach the security of your home WiFi and potentially cause you significant harm. Your home network may be used by malicious cyber...
The Secret Vulnerability Finance Execs are Missing
The (Other) Risk in Finance
A few years ago, a Washington-based real estate developer received a document link from First American – a financial...
New S1deload Malware Hijacking Users’ Social Media Accounts and Mining Cryptocurrency
Feb 23, 2023Ravie LakshmananCryptocurrency / Malware
An active malware campaign has set its sights on Facebook and YouTube users by leveraging a new information...
VMware Patches Critical Vulnerability in Carbon Black App Control Product
Feb 22, 2023Ravie LakshmananVulnerability / Enterprise Security
VMware on Tuesday released patches to address a critical security vulnerability affecting its Carbon Black App Control...
Gcore Thwarts Massive 650 Gbps DDoS Attack on Free Plan Client
Feb 22, 2023The Hacker NewsServer Security / DDoS Attack
At the beginning of January, Gcore faced an incident involving several L3/L4 DDoS attacks with...
Hydrochasma: New Threat Actor Targets Shipping Companies and Medical Labs in Asia
Feb 22, 2023Ravie LakshmananCyber Espionage / Cyber Attack
Shipping companies and medical laboratories in Asia have been the subject of a suspected espionage campaign...
3 Steps to Automate Your Third-Party Risk Management Program
Feb 22, 2023The Hacker NewsCyber Risk Management
If you Google "third-party data breaches" you will find many recent reports of data breaches that were...
Apple Privilege Escalation Bug Let Attacker Execute Arbitrary Code
Trellix researchers discovered a new class of privilege escalation bugs based on the ForcedEntry attack, which exploited a feature of macOS and iOS to...