New Technique Discovered To Bypass Web Application Firewalls
Experts from Industrial and IoT cybersecurity company Claroty developed a generic method for bypassing the web application firewalls (WAF) of a variety of leading manufacturers.
Following a...
New Go-based Malware Attack Windows & Linux Systems
The cybersecurity researchers at Lumen’s Black Lotus Labs asserted that in order to mine crypto-currencies and launch DDoS attacks, hackers are deploying an existing...
RCE Bug in ZOHO Products Let Hackers Execute Arbitrary Code Remotely
CISA’s bug catalog has been updated with a new vulnerability related to Java deserialization, which has been exploited in the wild by malicious threat...
Zerobot Botnet Emerges as a Growing Threat with New Exploits and Capabilities
Dec 22, 2022Ravie LakshmananInternet of Things / Patch Management
The Zerobot DDoS botnet has received substantial updates that expand on its ability to target...
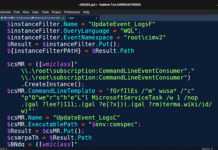
Chinese Espionage Hackers Target Tibetans Using New LOWZERO Backdoor
A China-aligned advanced persistent threat actor known as TA413 weaponized recently disclosed flaws in Sophos Firewall and Microsoft Office to deploy a never-before-seen backdoor...
LastPass Admits to Severe Data Breach, Encrypted Password Vaults Stolen
Dec 23, 2022Ravie LakshmananPassword Management / Data Breach
The August 2022 security breach of LastPass may have been more severe than previously disclosed by...
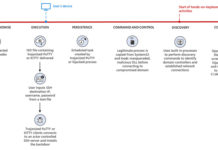
Researchers Uncover Covert Attack Campaign Targeting Military Contractors
A new covert attack campaign singled out multiple military and weapons contractor companies with spear-phishing emails to trigger a multi-stage infection process designed to...
Experts Uncover 85 Apps with 13 Million Downloads Involved in Ad Fraud Scheme
As many as 75 apps on Google Play and 10 on Apple App Store have been discovered engaging in ad fraud as part of...
Cisco Warns of High-Severity Unpatched Flaw Affecting IP Phones Firmware
Dec 10, 2022Ravie LakshmananEnterprise Security / IP Phones
Cisco has released a new security advisory warning of a high-severity flaw affecting IP Phone 7800...
North Korean Hackers Weaponizing Open-Source Software in Latest Cyber Attacks
A "highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering...