SSL Handshake (443 port of server at which SSL connection is made)
Client (Browser) ———————Client Hello Msg.————————————> Server
· Highest SSL Version
· Compression (SHA1, SHA1-DES)
· Cipher (zip, gzip..)
· Random Data
· MAC of client
Client (Browser) < ———————Server Hello Msg.———————————- Server
· Highest SSL Version
· Cipher + Compression
· Session ID
· Random Data ( Key Generation )
Client (Browser) < ———————Certificate-——————————————- Server
· Digital Signature
· Public Key (Identify by Web Page)
· Issued To, Issued By
· Valid From , Valid To
Client (Browser) < ———————Server Hello Done Msg.————————— Server
Client (Browser) ————————–Certificate Verify Msg.————————> Server
· Browser Verifies Server Certificate
Client (Browser) ——————-Change Cipher Spec (Command)——————-> Server
· Now the Browser will send every Data Encrypted in this Session
Client (Browser) —————————–Finished—————————————> Server
· Digest of all Messages (till now)
Client (Browser) <——————— Change Cipher Spec Msg.————————— Server
· Data send will be Encrypted
Client (Browser) < —————————- Finish Msg.———————————— Server
· Digest of all msg. (exchanged b/w )
· Public Key
Client (Browser) —————————–Symmetric SSL Key————————–> Server
Encrypted using Public Key
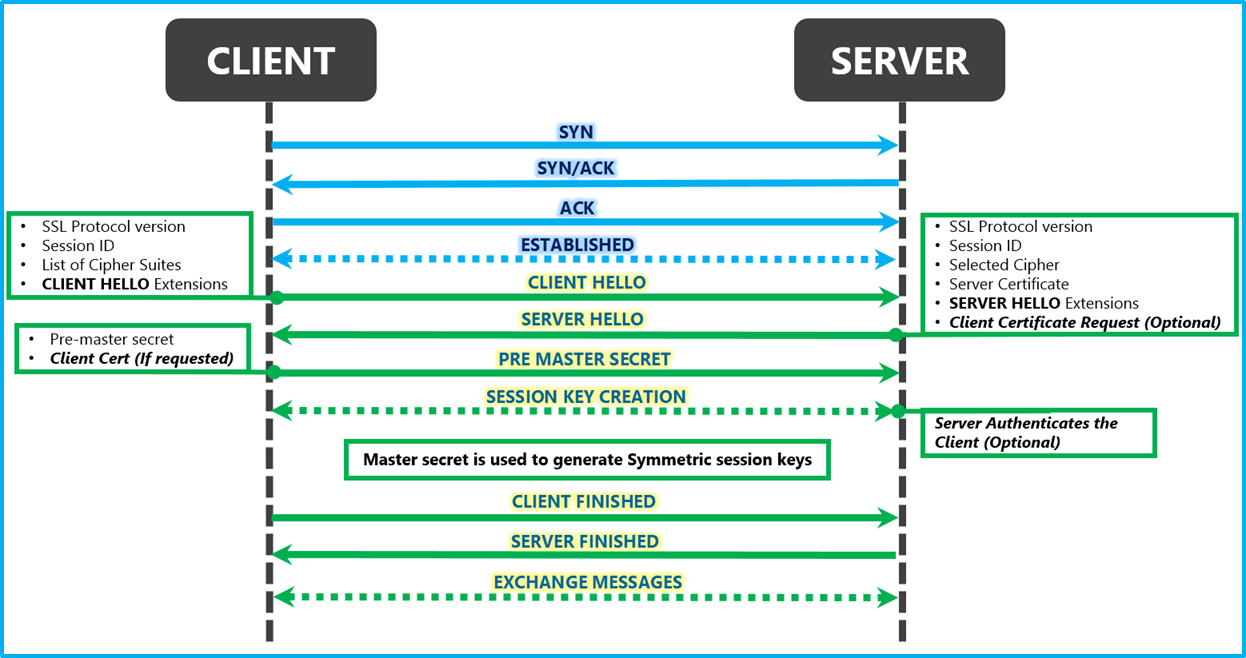
· Client key + Server Public Key ==> DATA===> Lock( Encrypted )
Now SSL Handshake Complete; Browser sends data (encrypted) over network to server
Client (Browser) —————————–Data Encrypted——————————-> Server
· Server Decrypts by Private Key
· If any msg. dropped; the SSL response breaks & Browser shows ERROR msg