Cybersecurity researchers have taken the wraps off a previously undocumented ransomware strain called Rorschach that’s both sophisticated and fast.
“What makes Rorschach stand out from other ransomware strains is its high level of customization and its technically unique features that have not been seen before in ransomware,” Check Point Research said in a new report. “In fact, Rorschach is one of the fastest ransomware strains ever observed, in terms of the speed of its encryption.”
The cybersecurity firm said it observed the ransomware deployed against an unnamed U.S.-based company, adding it found no branding or overlaps that connect it to any previously known ransomware actors.
However, further analysis of Rorschach’s source code reveals similarities to Babuk ransomware, which suffered a leak in September 2021, and LockBit 2.0. On top of that, the ransom notes sent out to the victims appear to be inspired by that of Yanluowang and DarkSide.
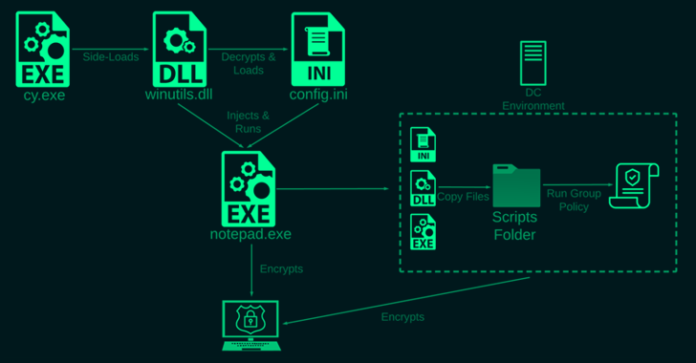
The most significant aspect of the intrusion is the use of a technique called DLL side-loading to load the ransomware payload, a method rarely observed in such attacks. The development marks a new sophistication in the approaches adopted by financially motivated groups to sidestep detection.
Specifically, the ransomware is said to have been deployed by abusing Palo Alto Network’s Cortex XDR Dump Service Tool (cy.exe) to sideload a library named “winutils.dll.”
Another unique characteristic is its highly customizable nature and the use of direct syscalls to manipulate files and bypass defense mechanisms.
Rorschach ransomware is also tasked with terminating a predefined list of services, deleting shadow volumes and backups, clearing Windows events logs to erase forensic trail, disabling the Windows firewall, and even deleting itself after completing its actions.
Internal propagation is achieved by compromising the domain controller and creating a group policy, according to Check Point and South Korean cybersecurity company AhnLab, which erroneously attributed the infection chain to DarkSide earlier this February.
The ransomware, like other malware strains observed in the wild, skips machines that are located in the Commonwealth of Independent States (CIS) countries by checking the system language.
“The Rorschach ransomware employs a highly effective and fast hybrid-cryptography scheme, which blends the curve25519 and eSTREAM cipher hc-128 algorithms for encryption purposes,” researchers Jiri Vinopal, Dennis Yarizadeh, and Gil Gekker explained.
This process is designed to only encrypt a specific portion of the original file content instead of the entire file, and employs additional compiler optimization methods that make it a “speed demon.”
In five separate tests carried out by Check Point in a controlled environment, 220,000 files were encrypted using Rorschach within four minutes and 30 seconds on average. LockBit 3.0, on the other hand, took approximately seven minutes.
“Its developers implemented new anti-analysis and defense evasion techniques to avoid detection and make it more difficult for security software and researchers to analyze and mitigate its effects,” the researchers said.
“Additionally, Rorschach appears to have taken some of the ‘best’ features from some of the leading ransomwares leaked online, and integrated them all together. In addition to Rorschach’s self-propagating capabilities, this raises the bar for ransom attacks.”
The findings come as the Fortinet FortiGuard Labs detailed two emerging ransomware families called PayMe100USD, a Python-based file-locking malware, and Dark Power, which is written in the Nim programming language.
Rorschach (aka BabLock) Attacks Spotted in Asia, Europe, and the Middle East
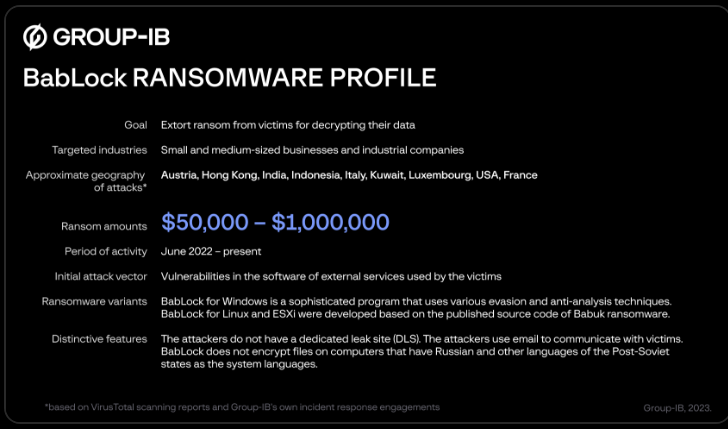
Singapore-headquartered Group-IB said it has identified Rorschach attacks targeting small and medium-sized companies and industrial firms across Asia, Europe, and the Middle East.
The cybersecurity company has christened the ransomware strain BabLock, so named for its source code similarities to Babuk and LockBit. It’s said to be active since at least June 2022 and has capabilities to strike ESXi and Linux systems as well.
“The absence of [a data leak site], along with relatively modest ransom requests ranging from 50,000 to 1,000,000 USD, allows the group to operate stealthily and remain under the radar,” Group-IB researchers Andrey Zhdanov and Vladislav Azersky said.
In the incident aimed at an unnamed industrial sector company in Europe, the threat actors leveraged a remote code execution flaw impacting Zimbra Collaboration (CVE-2022-41352, CVSS score: 9.8) to gain initial access.
The attack entailed no data exfiltration prior to encryption, instead pressurizing victims to pay up by threatening to “attack your company again in the future” and “delete all your data from your networks.”
The Linux counterpart, according to Group-IB, is an 32-bit ELF binary written in Go 1.18.3, whereas the ESXi variant is a 64-bit program for Linux in ELF format compiled using GNU Compiler (GCC). Both the versions are based on the leaked Babuk ransomware source code.
“It would make more sense for the threat actors to use a simpler program based on Babuk to encrypt Windows systems, but they preferred developing their own, more sophisticated program, which overall is not similar to other families,” the researchers said.
Palo Alto Networks, in an informational bulletin released on April 4, said it’s aware of attacks leveraging its Cortex XDR Dump Service Tool to load the Rorschach payload, adding they don’t affect macOS and Linux platforms. It’s also expected to release a patch to address the issue next week.
“When removed from its installation directory, the Cortex XDR Dump Service Tool (cydump.exe), which is included with Cortex XDR agent on Windows, can be used to load untrusted dynamic link libraries (DLLs) with a technique known as DLL side-loading,” the cybersecurity company said.
“Rorschach ransomware uses a copy of this tool and this technique to evade detection on systems that do not have sufficient endpoint protection. When the Cortex XDR agent is installed on Windows and the Cortex XDR Dump Service Tool process is running from the installation path, it is not possible to side-load DLLs with this technique.”
Source: thehackernews.com