Enterprise communications software maker 3CX on Thursday confirmed that multiple versions of its desktop app for Windows and macOS are affected by a supply chain attack.
The version numbers include 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS.
The company said it’s engaging the services of Google-owned Mandiant to review the incident. In the interim, it’s urging its customers of self-hosted and on-premise versions of the software to update to version 18.12.422.
“3CX Hosted and StartUP users do not need to update their servers as we will be updating them over the night automatically,” 3CX CEO Nick Galea said in a post on Thursday. “Servers will be restarted and the new Electron App MSI/DMG will be installed on the server.”
Evidence available so far points to either a compromise of 3CX’s software build pipeline to distribute Windows and macOS versions of the app package, or alternatively, the poisoning of an upstream dependency. The scale of the attack is currently unknown.
The earliest period of potentially malicious activity is said to have been detected on or around March 22, 2023, according to a post on the 3CX forum, although preparations for the campaign are said to have commenced no later than February 2022.
3CX said the initial alert flagging a potential security problem in its app last week was treated as a “false positive” owing to the fact that none of the antivirus engines on VirusTotal labeled it as suspicious or malware.
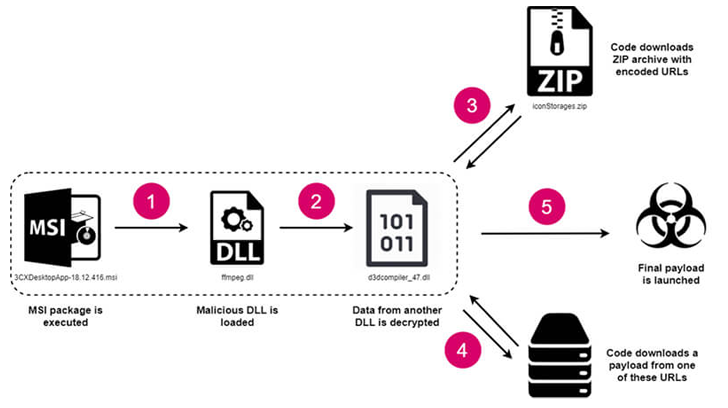
The Windows version of the attack leveraged a technique called DLL side-loading to load a rogue library referred to as “ffmpeg.dll” that’s designed to read encrypted shellcode from another DLL called “d3dcompiler_47.dll.”
This involved accessing a GitHub repository to retrieve an ICO file containing URLs hosting the final-stage payload, an information stealer (dubbed ICONIC Stealer or SUDDENICON) capable of harvesting system information and sensitive data stored in web browsers.
“The choice of these two DLLs – ffmpeg and d3dcompiler_47 – by the threat actors behind this attack was no accident,” ReversingLabs security researcher Karlo Zanki said.
“The target in question, 3CXDesktopApp, is built on the Electron open source framework. Both of the libraries in question usually ship with the Electron runtime and, therefore, are unlikely to raise suspicion within customer environments.”
 |
| SUDDENICON downloading a new executable |
The macOS attack chain, in the same vein, bypassed Apple’s notarization checks to download an unknown payload from a command-and-control (C2) server that’s currently unresponsive.
“The macOS version does not use GitHub to retrieve its C2 server,” Volexity said, which is tracking the activity under the cluster UTA0040. “Instead, a list of C2 servers is stored in the file encoded with a single byte XOR key, 0x7A.”
Cybersecurity firm CrowdStrike, in an advisory of its own, has attributed the attack with high confidence to Labyrinth Chollima (aka Nickel Academy), a North Korea-aligned state-sponsored actor.
“The activity, which targets many organizations across a broad range of verticals without any obvious patterns, has been attributed to Labyrinth Chollima based on observed network infrastructure uniquely associated with that adversary, similar installation techniques, and a reused RC4 key,” Adam Meyers, senior vice president of intelligence at CrowdStrike, told The Hacker News.
“The trojanized 3CX applications invoke a variant of ArcfeedLoader, malware uniquely attributed to Labyrinth Chollima.”
Labyrinth Chollima, per the Texas-based company, is a subset of the Lazarus Group, which also constitutes Silent Chollima (aka Andariel or Nickel Hyatt) and Stardust Chollima (aka BlueNoroff or Nickel Gladstone).
The group “has been active at least since 2009 and typically tries to generate revenue by targeting crypto and financial organizations,” Meyers said, adding it’s “likely affiliated with Bureau 121 of the DPRK’s Reconnaissance General Bureau (RGB) and primarily conducts espionage operations and revenue generation schemes.”
Source: thehackernews.com










