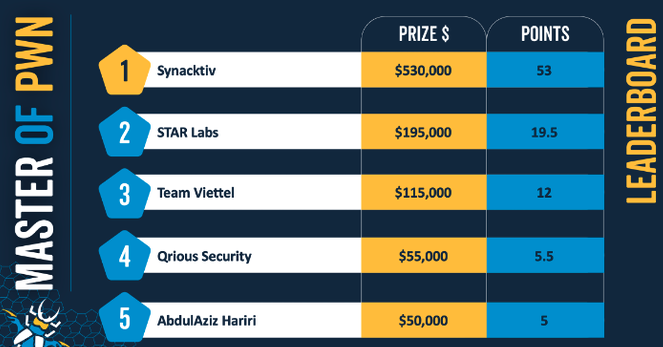
After the finale of Pwn2Own Vancouver 2023, the Masters of Pwn, Synacktiv (@Synacktiv), received $1,035,000 (plus a car) for their amazing achievements and hard work! They received a Tesla Model 3 and 53 points, along with $530,000.
The annual computer hacking competition benefits the cybersecurity sector in a number of ways. Over 19 entries participated in this year’s Pwn2Own 2023, hosted in Vancouver between March 22 and 24, 2023, and targeted nine platforms, including Tesla cars.
During the hacking competition, security researchers targeted devices in the enterprise applications and communications, local escalation of privilege (EoP), virtualization, servers, and automotive categories, all updated and in their default configuration.
This time, for every successful exploit, participants received the full prize (more than $1,000,000).
AbdulAziz Hariri of Haboob SA, who completed his attack against Adobe Reader utilizing a 6-bug logic chain leveraging many failed fixes that escaped the sandbox and overcame a banned API list, gave the first demonstration of the day. 5 Master of Pwn points and $50,000 are awarded to him.
Microsoft SharePoint was the target of a 2-bug chain that STAR Labs was able to run. They receive 10 Master of Pwn points and $100,000. Team STAR Labs also successfully carried out an attack against Ubuntu Desktop. They received $15,000 and 1.5 points for this, but it was a well-known exploit.
Oracle VirtualBox was exploited by Bien Pham (@bienpnn) of Qrious Security (@qriousec) via an OOB Read and a stacked-based buffer overflow. 4 Master of Pwn points and $40,000 are awarded to him.
Tesla – Gateway was the target of a TOCTOU attack by Synacktiv (@Synacktiv). They receive a Tesla Model 3 and $100,000, and 10 Master of Pwn points. Also, they made $40,000 by escalating their privileges on Apple macOS using a TOCTOU zero-day issue.
Marcin Wizowski used an improper input validation bug to elevate privileges on Windows 11. He receives $30,000 and 3 Master of Pwn points.
Thomas Imbert (@masthoon) and Thomas Bouzerar (@MajorTomSec) of Synacktiv (@Synacktiv) showed a three-bug chain against Oracle VirtualBox with a host EoP. There was already one bug in existence. In addition, they receive 8 Master of Pwn points and $80,000.
Also, Tesla – Infotainment Unconfined Root was exploited by David Berard (@ p0ly_) and Vincent Dehors (@vdehors) of Synacktiv (@Synacktiv) via a heap overflow and an OOB write. After collecting $250,000 and 25 Master of Pwn points, they are eligible for a Tier 2 reward.
In the Ubuntu Desktop, Tanguy Dubroca (@SidewayRE) of Synacktiv (@Synacktiv) employed an incorrect pointer scaling, leading to privilege escalation. $30k and 3 Master of Pwn points are theirs to keep.
Microsoft Teams was also hacked by Team Viettel (@vcslab) using a 2-bug chain, earning them $75,000 and 8 Master of Pwn points. Again, Oracle VirtualBox was exploited by dungdm (@ piers2) of Team Viettel (@vcslab) using an uninitialized variable and a UAF flaw. They get $40,000 and 4 Master of Pwn points.
Highlights from Day 3:
Kyle Zeng of ASU SEFCOM used a double-free flaw to exploit Ubuntu Desktop, earning $30,000 and three Master of Pwn points.
Thomas Imbert of Synacktiv used a UAF against Windows 11. Three Master of Pwn points and $30,000 were awarded to Imbert. Mingi Cho from Theori also utilized a UAF to attack Ubuntu Desktop. Three Master of Pwn points and a $30,000 bounty were awarded to Chio.
To attack VMware Workstation, STAR Labs (@starlabs sg) exploited an uninitialized variable and UAF. They receive $80,000 in addition to 8 Master of Pwn points.
Bien Pham (@bienpnn) of Qrious Security successfully targeted Ubuntu Desktop. However, the exploit was previously known. Still, they receive $15,000 and 1.5 Master of Pwn points.
Following successful hacks of Windows 11, Microsoft Teams, Microsoft SharePoint, macOS, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox, and, of course, the Tesla Model 3, the hackers were able to escalate their privileges and obtain code execution on systems with all necessary patches.
Notably, vendors have 90 days to deliver security updates after Pwn2Own, when zero-day vulnerabilities are exploited and disclosed before TrendMicro’s Zero Day Initiative makes them public.
Searching to secure your APIs? – Try Free API Penetration Testing
Related Coverage:
Source: gbhackers.com











