In response to a recent vulnerability identified in Outlook, Microsoft recently published a proper guide for its customers to help them discover the associated IoCs.
That Outlook vulnerability in question has been tracked as “CVE-2023-23397” with a CVSS score of 9.8 and marked as Critical.
As a result of this flaw, NTLM hashes can be stolen, and without any user interaction, they can be reused to execute a relay attack.
The threat actors use specially crafted malicious emails to exploit the vulnerability and manipulate the victim’s connection. As a result, this allows them to get control of an untrusted location.
The attacker can authenticate as the victim with the Net-NTLMv2 hash leaked to the untrusted network.
Microsoft patched the flaw
In the Patch Tuesday updates for March 2023, Microsoft fixed the vulnerability in order to prevent the possibility of any further attacks.
The problem is that this approach was taken after it was weaponized by Russian threat actors and used as a weapon against the following sectors in Europe:
- Government
- Transportation
- Energy
- Military
It was reported in April 2022 that Microsoft’s incident response team had found evidence that the shortcoming could be exploited.
Attack chain & threat hunting Guidance
It has been identified that a Net-NTLMv2 Relay attack allowed a threat actor to gain unauthorized entry to an Exchange Server in one attack chain.
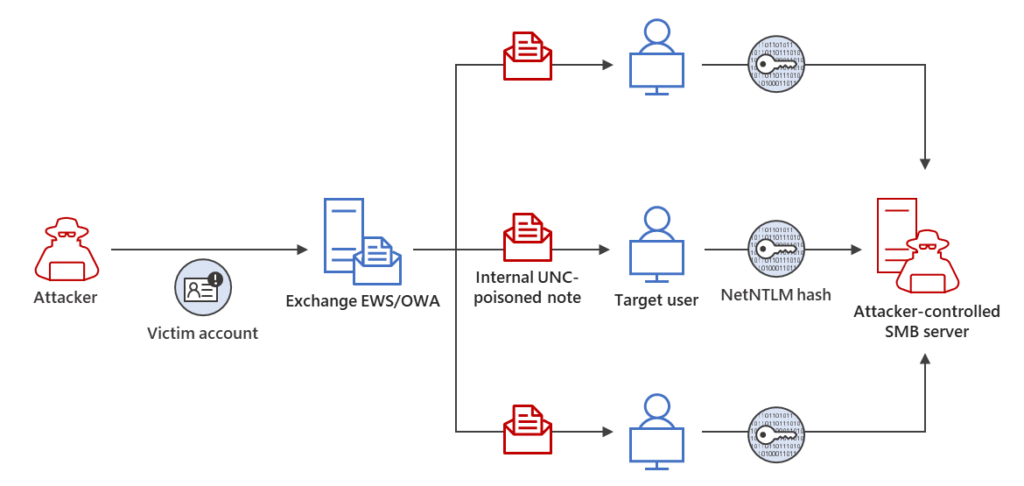
By exploiting this vulnerability, the attacker could modify mailbox folder permissions and maintain persistent access, posing a significant security risk.
The adversary used the compromised email account in the compromised environment to extend their access. It has been discovered that this is done by sending additional malicious messages through the same organization to other members.
CVE-2023-23397 can lead to credential compromise in organizations if they do not implement a comprehensive threat-hunting strategy.
As a first step, running the Exchange scanning script provided by Microsoft is important to detect any malicious activity. However, it’s imperative to note that for all scenarios, this script is not capable of providing any visibility into messages that are malicious in nature.
Multiple mailboxes can be opened at the same time by Outlook users. Messages received through one of the other services will still trigger the vulnerability if a user configured Outlook to open mailboxes from multiple services. The scanned mailboxes do not contain that message.
If a user wishes to move a message to a local file, they can do so. Finding evidence of a prior compromise in Archived messages may be possible in some cases.
You can no longer access your Exchange messages if they have been deleted from Exchange. It is recommended that incident responders review the security telemetry collected from all available channels in order to confirm the presence of IP addresses and URIs obtained from the PidLidReminderFileParameter values.
There are a number of data sources that can be used to gather data, including:-
- Firewall logs
- Proxy logs
- Azure Active Directory sign-in logs for users of Exchange Online
- IIS Logs for Exchange Server
- VPN logs
- RDP Gateway logs
- Endpoint telemetry from endpoint detection and response (EDR)
- Forensic endpoint data
Recommendations
Here below we have mentioned all the recommendations:-
- To mitigate the issue, make sure to update Microsoft Outlook immediately.
- Ensure that defense-in-depth mitigations are active in organizations leveraging Microsoft Exchange Server on-premises.
- The script should be used to remove either the messages or just the properties if suspicious or malicious reminder values are observed.
- In the event that a targeted or compromised user receives suspicious reminders or initiates incident response activities, they should be instructed to reset their passwords.
- To mitigate the impact of possible Net-NTLMv2 Relay attacks, it is recommended that you use multifactor authentication.
- On Exchange, you should disable unnecessary services that you don’t need.
- Block all IP addresses except those on an allowlist from requesting connections on ports 135 and 445.
- If your environment has NTLM enabled, you should disable it.
Searching to secure your APIs? – Try Free API Penetration Testing
Related Coverage
Source: gbhackers.com











