In 2022, the number of new mobile banking Trojan installers found by Kaspersky Lab’s cybersecurity researchers surged to 196,476, which is more than twice the number reported in 2021.
This alarming statistic underscores the increasing sophistication and frequency of cyberattacks on mobile devices. The proliferation of mobile banking Trojans has reached an unprecedented level, marking the highest surge observed in the past six years.
The fact that cybercriminals are actively targeting mobile users and prioritizing the theft of financial data is becoming increasingly apparent. This trend is further reinforced by the significant investments being made in the creation of new malware designed to exploit vulnerabilities in mobile devices.
The growing sophistication of these attacks poses a major threat to the financial well-being of their targets, with the potential for significant financial losses.
Newly Discovered Banking Malware
In 2022, cybersecurity experts uncovered the presence of multiple mobile Trojan subscribers on the Google Play Store. A number of banking Trojan families are still available on Google Play that is disguised as utilities, including:-
Cybersecurity researchers have identified a new mobile Trojan family, known as Harly, that has been active since 2020. This new threat has been added to the list of known mobile Trojan families, which includes Jocker and MobOk.
In 2022, a staggering 2.6 million downloads of Harly malware programs were recorded from Google Play, the official app store for Android devices. In the previous year, cybercriminals took advantage of the Google Play Store to disseminate a range of fraudulent apps that promised enticing incentives, such as:-
- Welfare payments
- Lucrative energy investments
The Sharkbot Trojan has been found to be actively distributing downloaders that imitate file manager apps. These downloaders are designed to request permission to install additional packages required for the Trojan to function effectively on the user’s device.
However, granting such permissions could expose the user’s device to potential security breaches, thereby putting their sensitive information at risk.
Trends Going Surge
According to a recent analysis, mobile attacks experienced a gradual decline in the latter half of 2021 and throughout 2022 plateaued at approximately the same level.
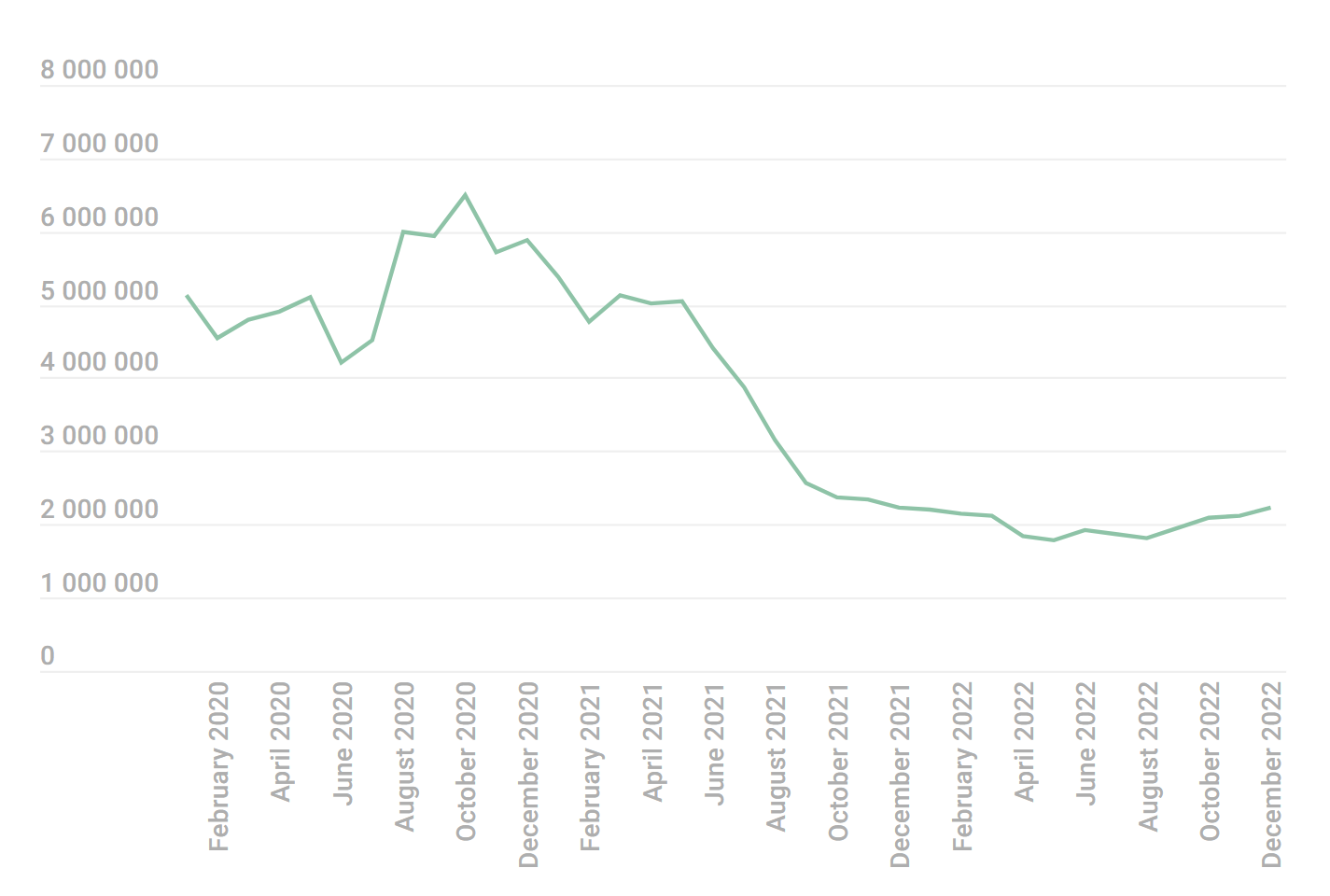
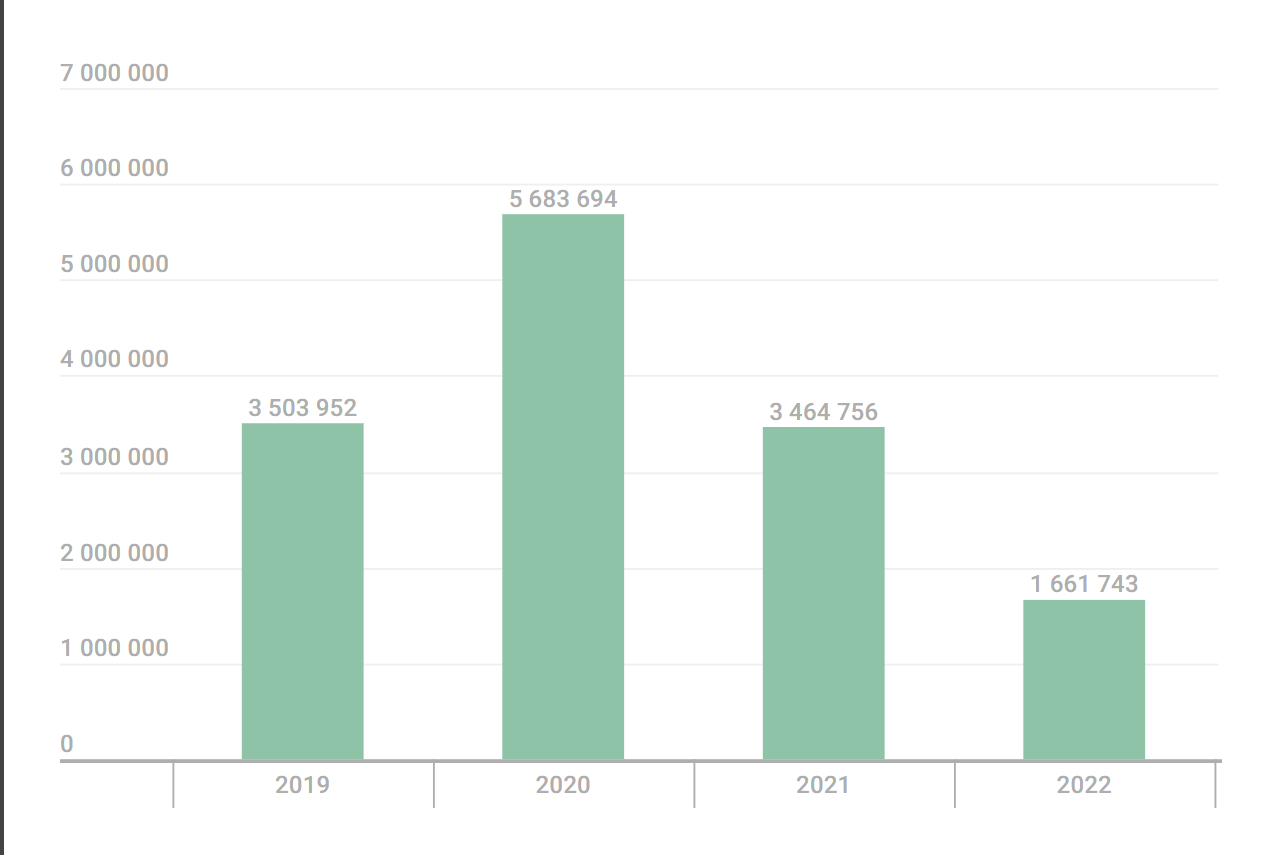
In 2022, a significant decline of 1,803,013 malware or unwanted software installers was detected by experts, as compared to the previous year. A total of 1,661,743 malware or unwanted software installers were identified by experts in the past year.
In 2022, the rankings for potentially unwanted software witnessed a shift, with RiskTool-type software taking the lead with 27.39% prevalence. Adware, which was the previous leader, has been replaced and now accounts for 24.05% of the total unwanted software detected.
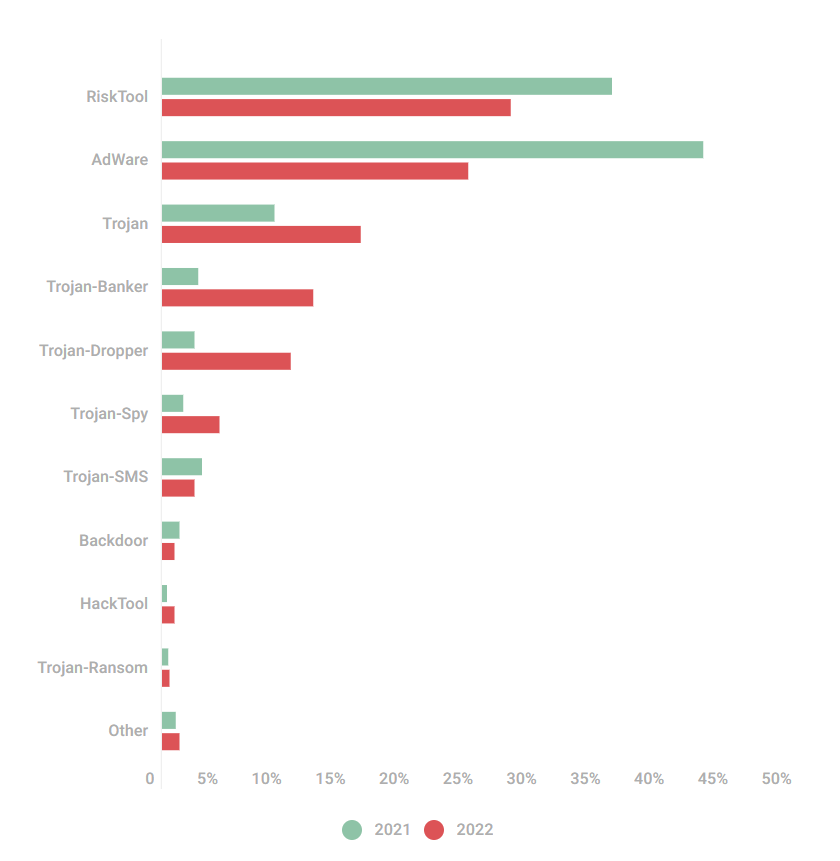
In comparison to 2021, there has been a significant decrease in the share of RiskTool and adware software in 2022. RiskTool witnessed a decline of 7.89 percentage points, while adware witnessed a more significant decrease of 18.38 percentage points.
Trojan-type malware secured the third position in the rankings, accounting for 15.56% of the total malware detected in 2022. This is a notable increase of 6.7 percentage points from the previous year.
Cybercriminal activity in 2022 did not witness any significant changes, as the attack numbers remained steady after a decrease in the previous year. This indicates that the cybersecurity measures put in place by individuals and organizations are becoming more effective in preventing attacks.
Recommendations
Here below we have mentioned the recommendations offered by the security analysts at Kaspersky:-
- Only download apps from official app stores if you want to ensure the safety of your device.
- Before granting permission to an application, review the permissions of the app you are using.
- In order to detect malicious software and adware, it is important that you use a reliable security solution.
- If you believe that apps should not have access to photos, contacts, or GPS features, Apple provides some privacy controls to block them.
- Ensure that your operating system as well as essential apps are always up-to-date.
Network Security Checklist – Download Free E-Book
Source: gbhackers.com











